How to Install Splunk Enterprise and Universal Forwarder on AWS EC2
Introduction
This blog walks you through setting up Splunk Enterprise (Master) and a Universal Forwarder (Slave) on AWS EC2 instances. It also covers the core components of Splunk, configuration steps, and how to run basic queries. If you haven’t already set up your AWS EC2 instances, follow the instructions in my previous blog post,Guide to Creating an EC2 Instance before proceeding.
Table of Contents
- Prerequisites
- Splunk Master Installation
- Splunk Slave Installation (Universal Forwarder)
- Key Components of Splunk
- Configuration
- Adding Data Sources
- Running Queries in Splunk
Prerequisites
Before you begin the installation, ensure that:
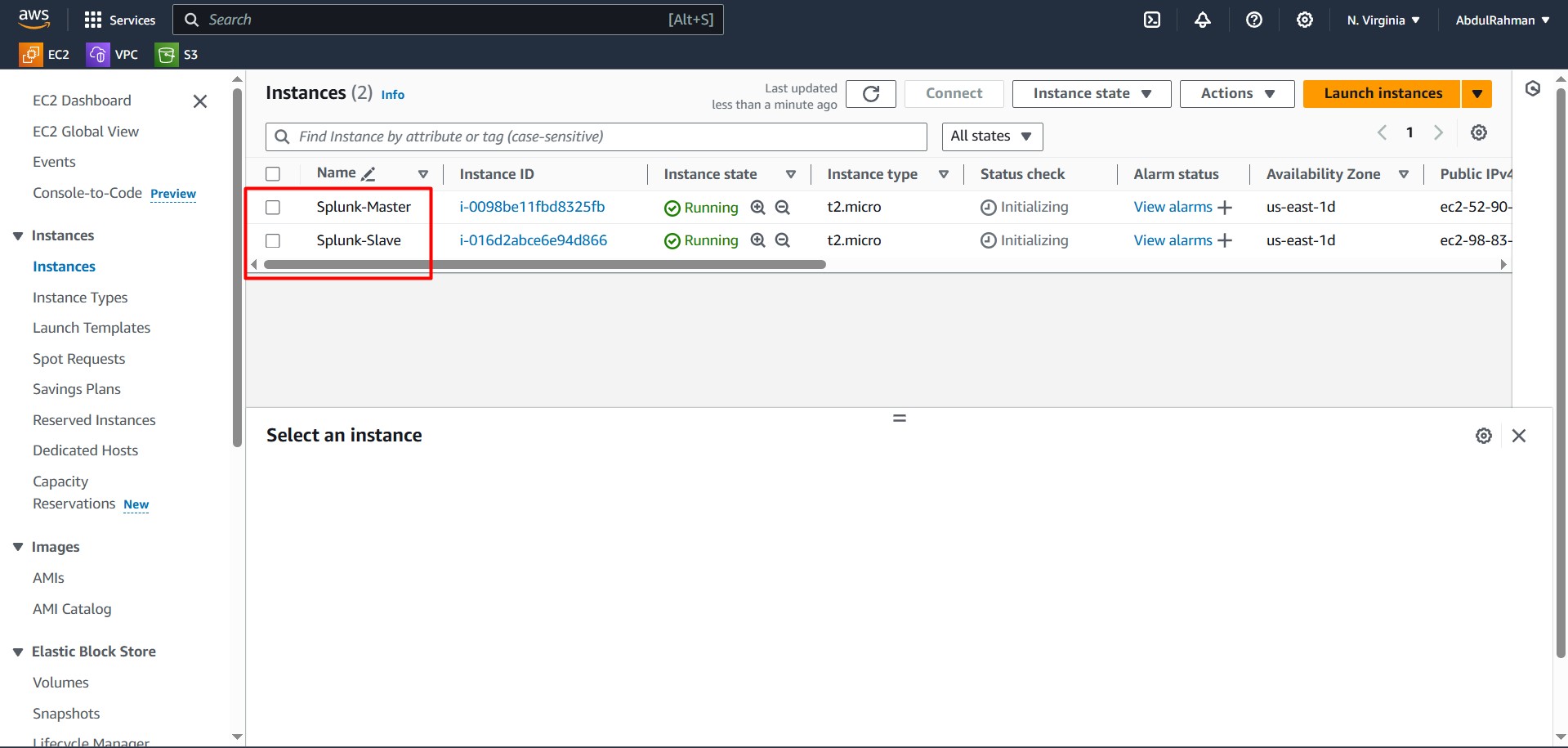
- You have two AWS EC2 instances: one for the Splunk Master (Enterprise) and one for the Splunk Slave (Universal Forwarder).
- You have SSH access to both instances.
- You have downloaded the Splunk packages from the official Splunk download page.
 If you need assistance setting up the servers, refer to my detailed guide on Guide to Creating an EC2 Instance before proceeding
If you need assistance setting up the servers, refer to my detailed guide on Guide to Creating an EC2 Instance before proceeding
Splunk Master Installation
Here are the steps to install Splunk Enterprise on the master EC2 instance:
- Navigate to the
/optdirectory:cd /opt - Download the Splunk package:
wget -O splunk-8.2.6-a6fe1ee8894b-Linux-x86_64.tgz https://download.splunk.com/products/splunk/releases/8.2.6/linux/splunk-8.2.6-a6fe1ee8894b-Linux-x86_64.tgz - Extract the package:
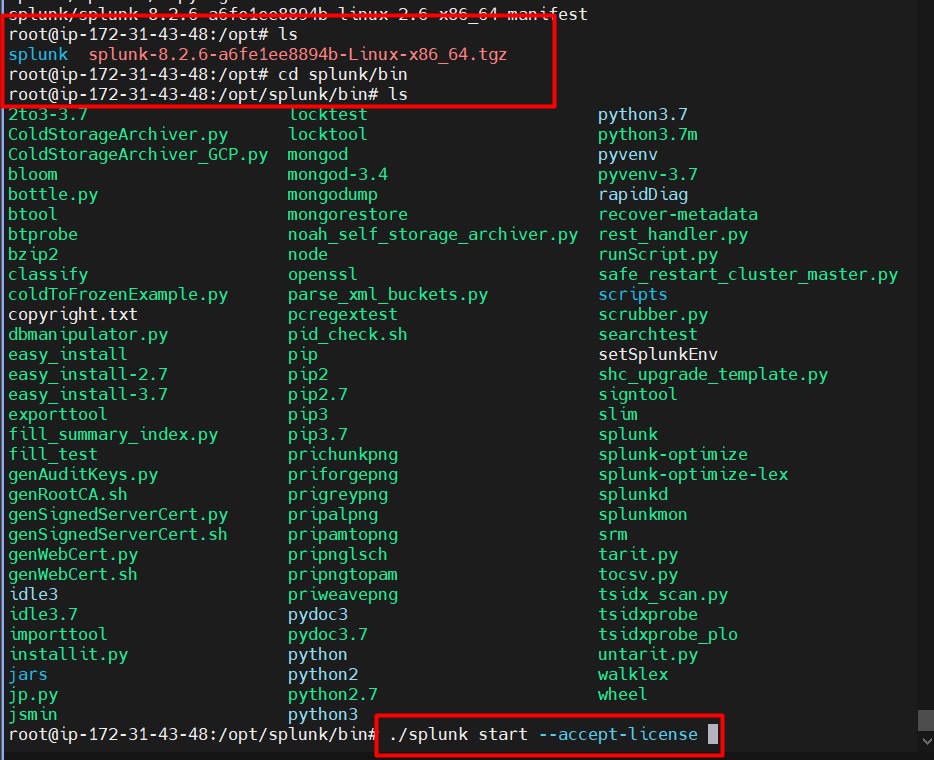
tar -xvzf splunk-8.2.6-a6fe1ee8894b-Linux-x86_64.tgz cd splunk/bin - Start Splunk:
./splunk start --accept-license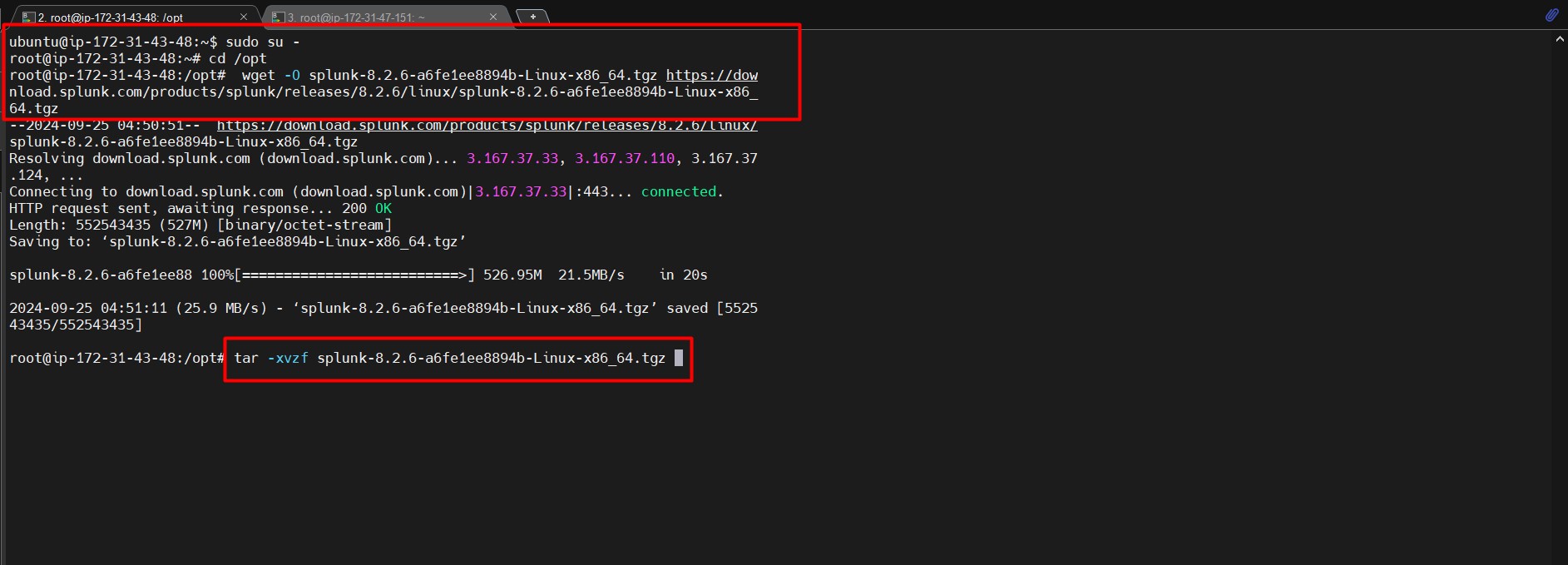
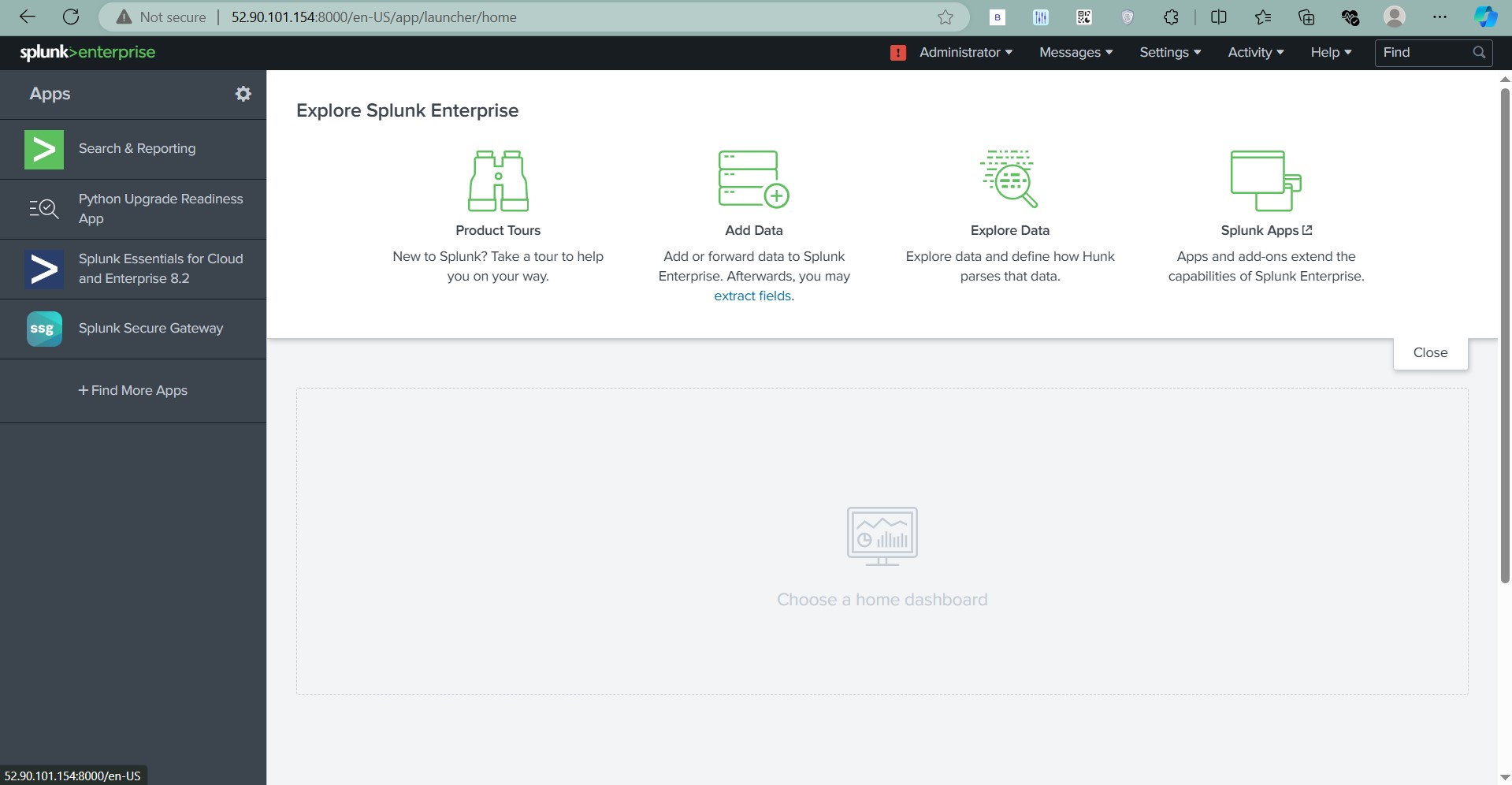
- Access the Splunk Web Interface by visiting the following URL:
http://<your-master-ip>:8000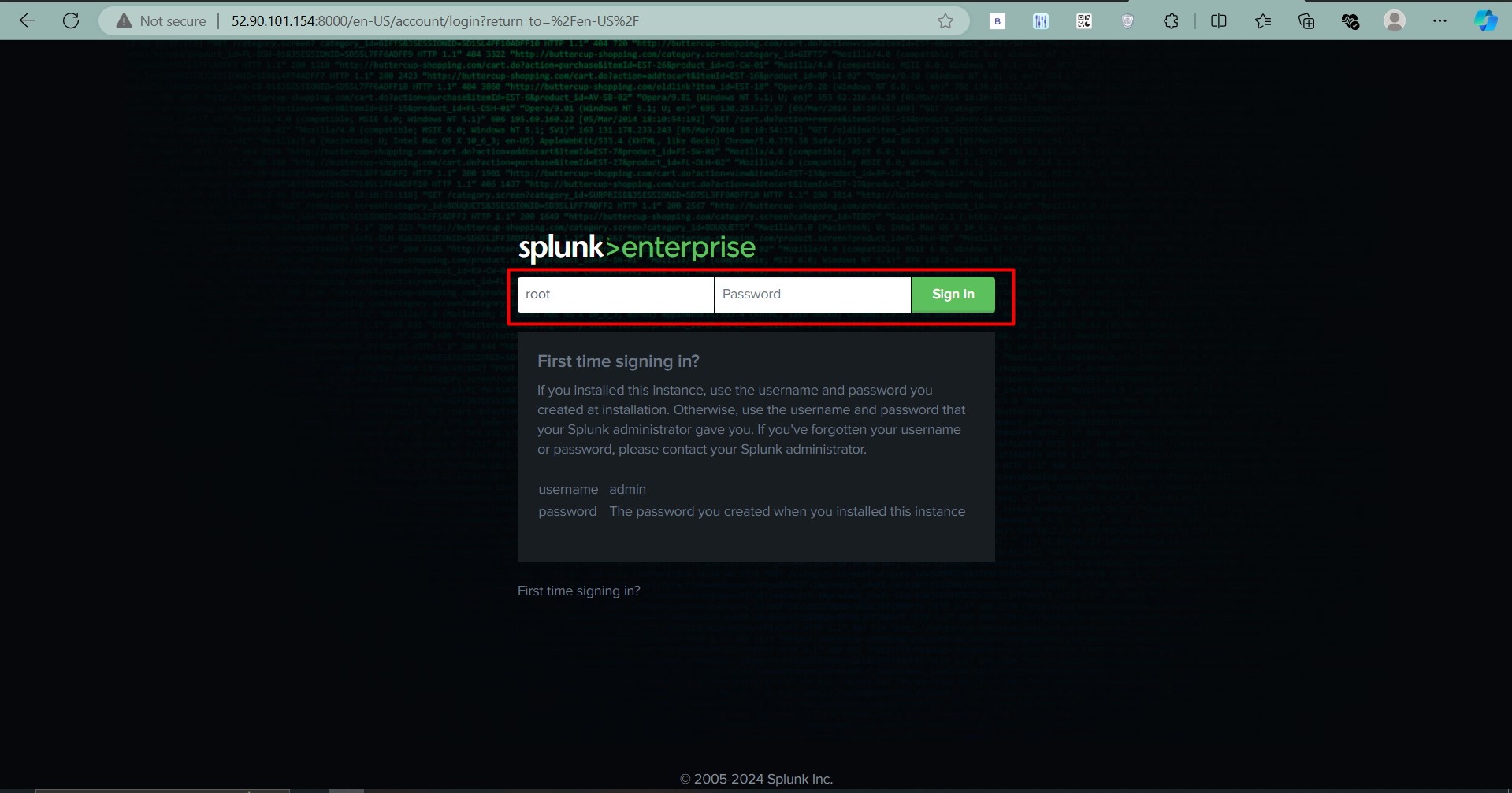
- Log in with default credentials:
- Username:
root - Password:
12345678(change this on first login).
- Username:
Splunk Slave Installation (Universal Forwarder)
To install the Splunk Universal Forwarder on the slave EC2 instance:
- Navigate to the
/optdirectory:cd /opt - Download the Universal Forwarder package:
wget -O splunkforwarder-8.2.6-a6fe1ee8894b-Linux-x86_64.tgz https://download.splunk.com/products/universalforwarder/releases/8.2.6/linux/splunkforwarder-8.2.6-a6fe1ee8894b-Linux-x86_64.tgz - Extract the package:
tar -xvzf splunkforwarder-8.2.6-a6fe1ee8894b-Linux-x86_64.tgz cd splunkforwarder/bin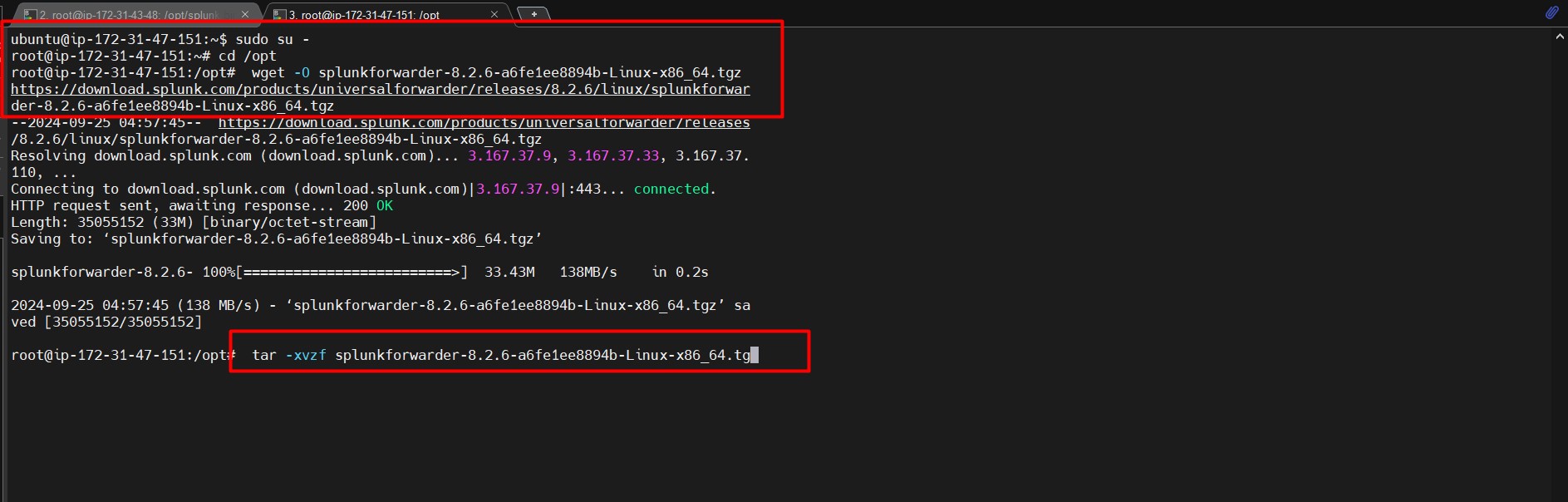
- Start the Splunk Forwarder:
./splunk start --accept-license - Create credentials:
- Username:
root - Password:
12345678
- Username:
Key Components of Splunk
Splunk is built on three essential components:
- Search Head: The interface where you can search, analyze, and visualize data.
- Indexer: Indexes and stores incoming data for quick searches.
- Forwarder: Collects data from various sources and forwards it to the indexer.
These components work together to form a powerful data monitoring and analysis system.
Configuration
Master Configuration
- Enable the Master Server to listen on port
9997:./splunk enable listen 9997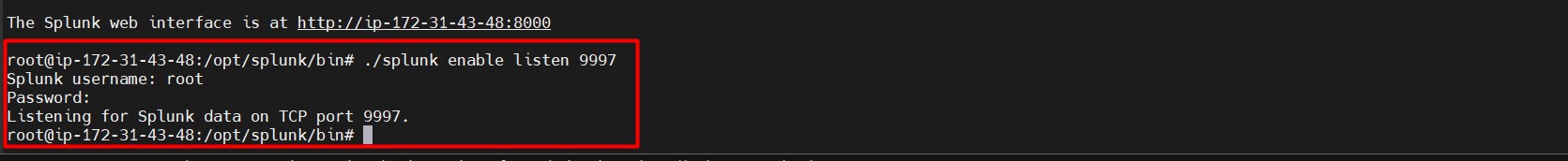
Slave Configuration
- Add the Master Server’s IP to the Slave (Forwarder) configuration:
./splunk add forward-server <master-ip>:9997 - Enter Master node credentials:
- Username:
root - Password:
12345678
- Username:
Adding Data Sources
To forward data, such as syslog, from the Slave to the Master:
- Add a syslog file to monitor:
./splunk add monitor /var/log/syslog --index main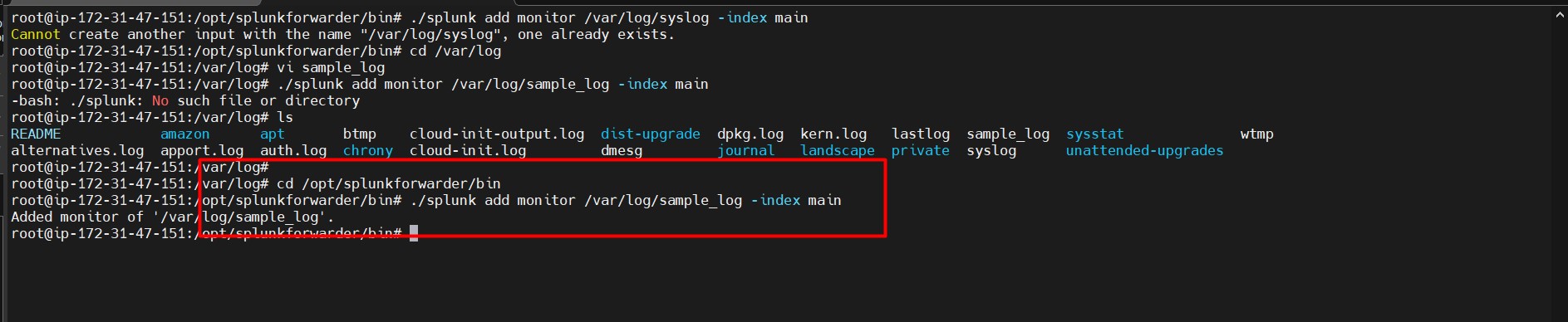
- Alternatively, add a sample log file:
cd /var/log vi sample_logEnter the sample logs here and save the file. Then navigate back to the Splunk directory:
cd /opt/splunkforwarder/binAdd the sample log for monitoring:
./splunk add monitor /var/log/sample_log --index main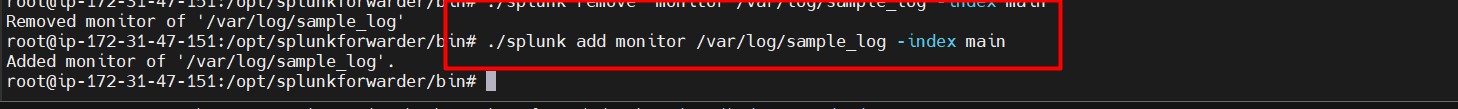
- Splunk will start indexing the log files from the specified path.
Running Queries in Splunk
Once the data is indexed, you can run queries to retrieve and analyze the data.
Example Query
index="main" host="slave-node" source="/var/log/syslog" sourcetype="syslog"
or simply:
index="main"
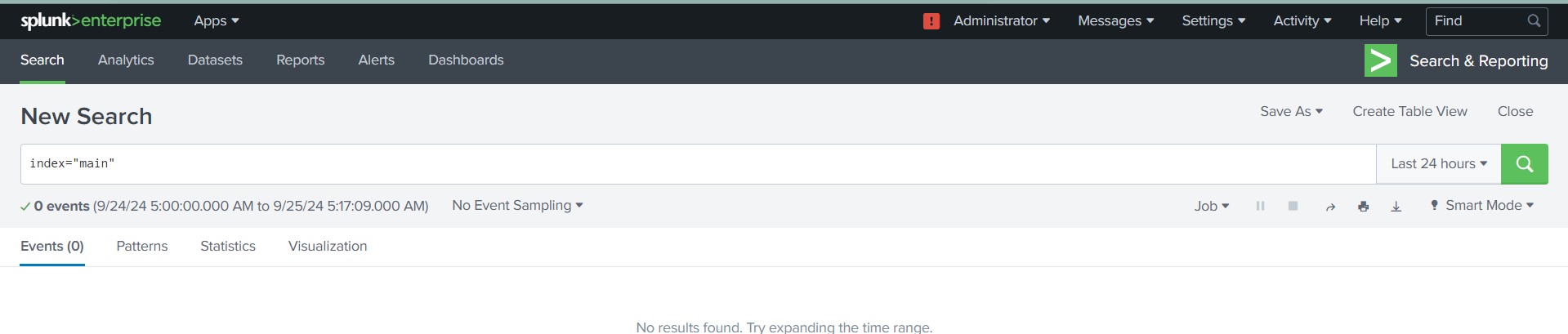
This query will fetch logs from the main index where the source is /var/log/syslog.
By following this guide, you have successfully installed Splunk Enterprise and a Universal Forwarder, configured them, and added data sources. Now, you’re ready to dive deeper into Splunk’s capabilities!
For more information, visit the official Splunk documentation.

Leave a comment